Nowadays where cloud services are available from all over the world we cannot (only) rely on trusted networks and on identities protected by usernames and passwords. Conditional access allows you to define granular controls whether an identity can access cloud applications. Based on the positive feedback for my “5 Ways to Screw up your Intune Tenant” post I felt empowered to get conditional access covered as well.
Chose your platform wisely
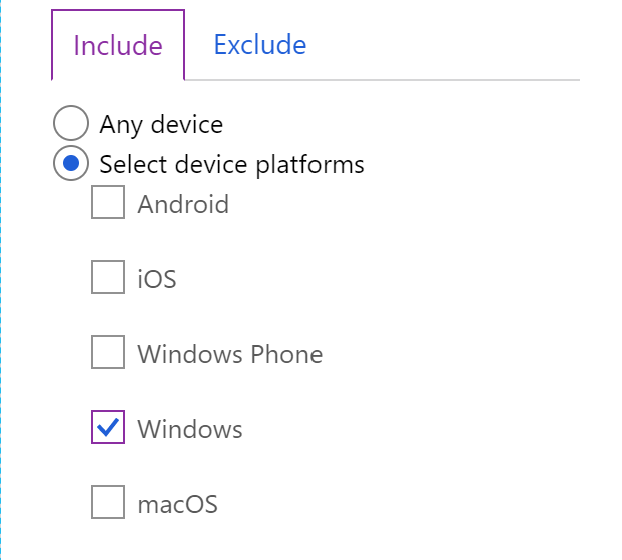
If you intend to use the device platform filter make sure that you cover all platforms including unknown platforms. Otherwise your might have a lack in your battleship. Also note that platform detection is based on best effort and can be exploited.
Long live legacy
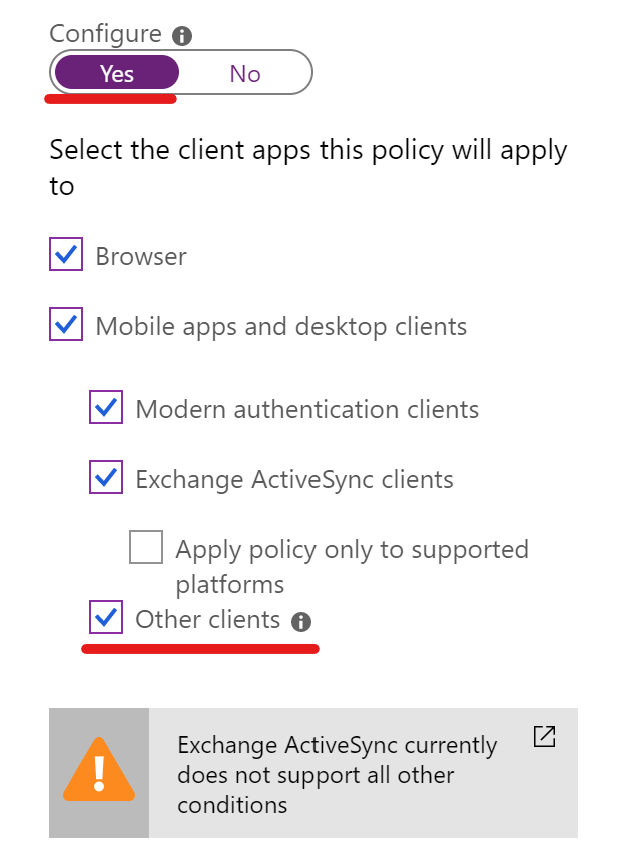
Mind the client apps configuration to ensure that your conditional access policies also apply to non-modern authentication clients. If you have created your conditional access policies in the early days of the product you didn’t have this option available.
Something that has created some confusion is that conditional access policies don’t include legacy authentication clients by default, this means that if you have a conditional access policy enforcing MFA for all users and all cloud apps, it doesn’t block legacy authentication clients (or “Other clients”, as the CA UI refers to them) - Sue Bohn, Microsoft
 |
|  |
|
All users aren’t the users you are looking for
When targeting a conditional access policy to “All users” and enforcing multi factor authentication or compliant devices you might want to reconsider your choice.
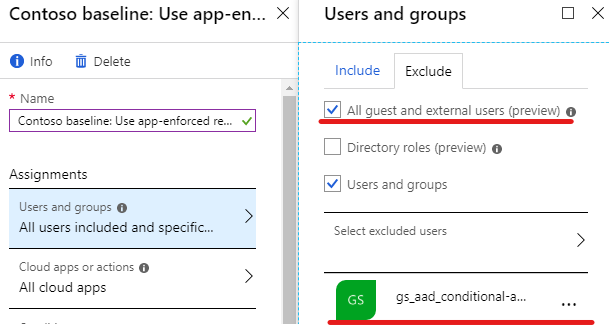
- Microsoft recommends to have at least two emergency access accounts (also referred to break glass accounts). Therefore you should exclude those accounts from all conditional access policies.
- Note that guest users are also targeted by the “All users” selection.
- If you have Azure AD Connect in place also exclude the “On-Premises Directory Synchronization Service Account” account located in Azure AD. Otherwise synchronization errors might occur if you enforce MFA on this account
For a simplified administration of these excluded accounts I recommend gathering them in an Azure Active Directory group. Besides that you have a good overview of which accounts are excluded.
Not keeping an eye on excluded accounts
Because you probably will have accounts not covered by conditional access policies (as mentioned above) it is important to keep an eye on them. If you have gathered these accounts in an Azure AD group you can monitor and audit all activities for this group and it’s members. Furthermore it could make sense to trigger an alert as soon as activities on those accounts occurs (except for the Azure AD Connect account).
To audit account activity you can use:
- Azure Active Directory Sign-Ins and Audit Logs
- Azure Log Analytics
- 3rd party monitoring solutions
For alerts:
- Azure Monitor Alerts (formerly known as Azure Log Analytics Alerts)
- Microsoft Cloud App Security
(Please note that both lists are non-exhaustive. I am curious about your solutions)
Azure AD audit logs forwarded to Azure Log Analytics and resulting Azure Monitor alerts are usually triggered after a delay. If your are looking for a solution with minimal delay for alerts Microsoft Cloud App Security might be your tool of choice. It offers various integrations regarding alerting by offering a Microsoft Flow connector and the native option to send text messages:
stratɪdʒi (having a strategy)
Probably one of the most important points when it comes to conditional access is to evaluate a strategy which fit’s your companies, end-users or customers needs and way of working. Try to find a balance between a security and usability. You might have to raise awareness and explain why conditional access is indispensable to harden cloud services which are accessible by specifying a username and password. From everywhere.
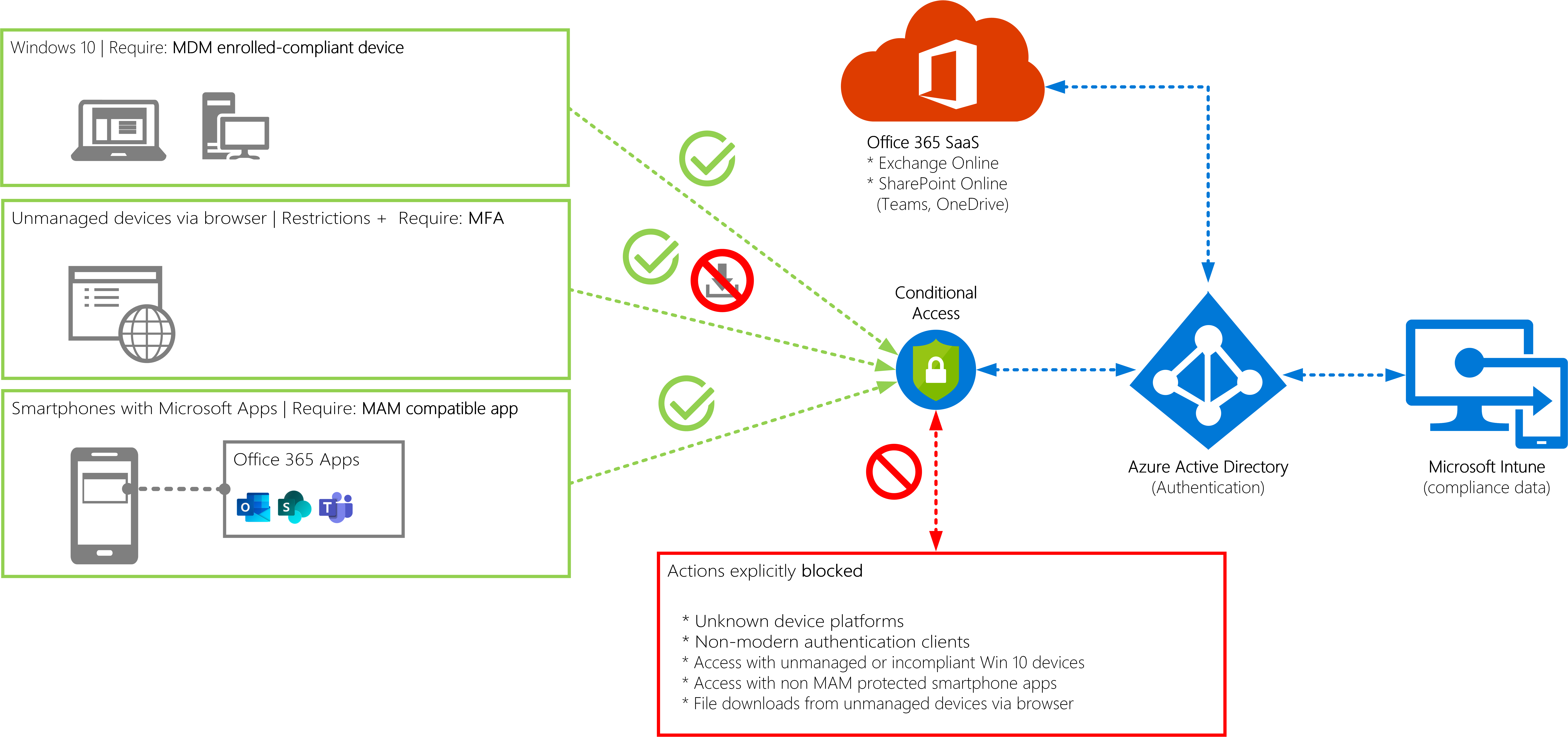
The image below represents a companies strategy which allows their employees to access Office 365 resources under the following circumstances:
- Corporate owned Windows 10 devices: Enrolled in Intune and compliant
- Personal owned smartphones (BYOD): Must use an approved client app because MAM policies are deployed with Intune
- Web browser access from unmanaged devices: MFA is enforced, additionally app enforced restrictions prevent file downloads
- Guest users are not affected by any rules whereas files shared with them are monitored with cloud app security
Visualized Conditional Access Strategy:
Also note that such a strategy requires a certain maturity and adoption of your end-users. A detailed testing and continuous development of your security posture (with conditional access) is inevitable.
Final words
Extemporaneous conditional access implementations without careful planning and testing in advance will mostly not succeed. So as a take-away message if you plan to use conditional access:
- Define your strategy. Ask yourself what do you want to achieve.
- Implement things. Test carefully. From an end user and administrator perspective.
- Audit and track configuration changes. Enjoy your modern and secure workplace. Tackle the next challenges.