Recently I got a DM on Twitter with a question about how to export and import Endpoint Security profiles with Microsoft Graph. Besides a technical answer which might be of interest for you, I’d like to show you the workflow I used to give a proper reply.
Original question:
Hi @nicolonsky, I was advised on the MS Elite Partner focus groups team (MEM Automation) to reach out to you regarding my question about export/import policies from Endpoint Security in Intune. I’ve been able to export the Disk Encryption policy (via graph explorer), but haven’t been able to find the correct format to use to upload/import it. I was hoping that you would be able to advise on how to go about achieving this.
Workflow
Discover request URL’s and payload
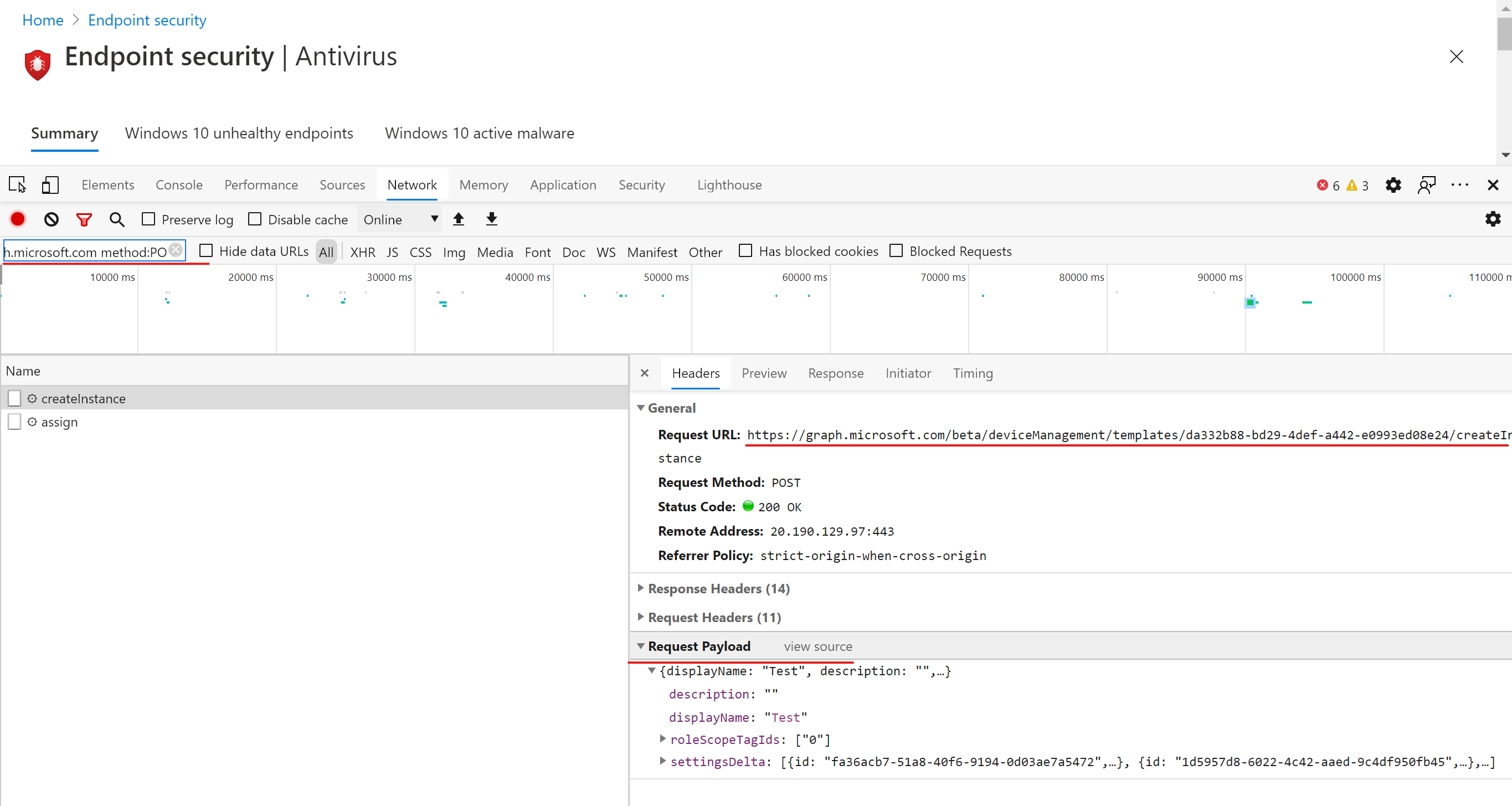
To discover the request URLs and payloads I used the methodology I explained in the this post a while ago. Basically, I tracked the network activity and used a filter to only include requests made to the Graph API while doing the following activities:
Creating a profile
POST: https://graph.microsoft.com/beta/deviceManagement/templates/2b595bcc-ef65-42ce-a0e3-67389ae50b8e/createInstance
{
"displayName": "test",
"description": "",
"settingsDelta": [
{
"id": "d172cbcc-030f-4b78-af35-c0791f584b1d",
"definitionId": "deviceConfiguration--windows10EndpointProtectionConfiguration_bitLockerFixedDrivePolicy",
"@odata.type": "#microsoft.graph.deviceManagementComplexSettingInstance",
"valueJson": "{\"encryptionMethod\":null,\"requireEncryptionForWriteAccess\":false,\"recoveryOptions\":{\"blockDataRecoveryAgent\":false,\"recoveryKeyUsage\":null,\"recoveryPasswordUsage\":null,\"hideRecoveryOptions\":false,\"enableRecoveryInformationSaveToStore\":false,\"recoveryInformationToStore\":null,\"enableBitLockerAfterRecoveryInformationToStore\":false}}"
}
],
"roleScopeTagIds": [
"0"
]
}
Viewing/editing a profile
GET: https://graph.microsoft.com/beta/deviceManagement/intents/23ead0f2-c79a-430a-a988-53939f1794fd/settings
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#deviceManagement/intents('23ead0f2-c79a-430a-a988-53939f1794fd')/settings",
"value": [
{
"@odata.type": "#microsoft.graph.deviceManagementBooleanSettingInstance",
"id": "33081642-09d8-4b8b-bdac-03d399dbaee2",
"definitionId": "deviceConfiguration--windowsIdentityProtectionConfiguration_unlockWithBiometricsEnabled",
"valueJson": "true",
"value": true
}
]
}
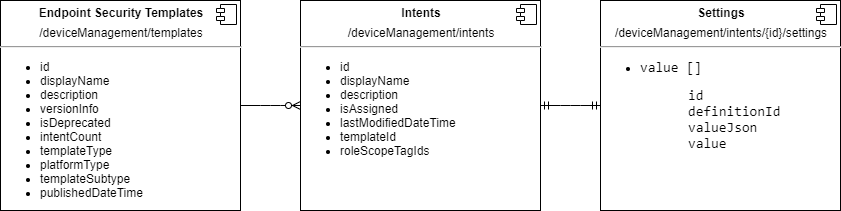
Understanding the data structure
Now I needed to understand how the different entities are linked together to get the necessary information for exporting a profile. This picture roughly describes how the entities are organized on the API (not accurate or valid UML though):
To construct an importable endpoint security profile I needed to:
- Rename the
value[]tosettingsDelta[] - Add the
displayNameanddescriptionproperties
To know to which template settings reference we also need to keep track of the templateId which is required for the import request URL.
We just need to make sure that we remove the templateId property before we pass the request body to the API.
Scripting
The last part was about putting together some PowerShell code that invokes the required requests and produces some JSON output which stores the serialized data.
I did not use any special module to do the API requests and just implemented the requests in different PowerShell functions for a more detailed example. To acquire an access token I always rely on the MSAL.PS module which is probably the best and most flexible way out there instead of writing custom methods to obtain access tokens.
Result
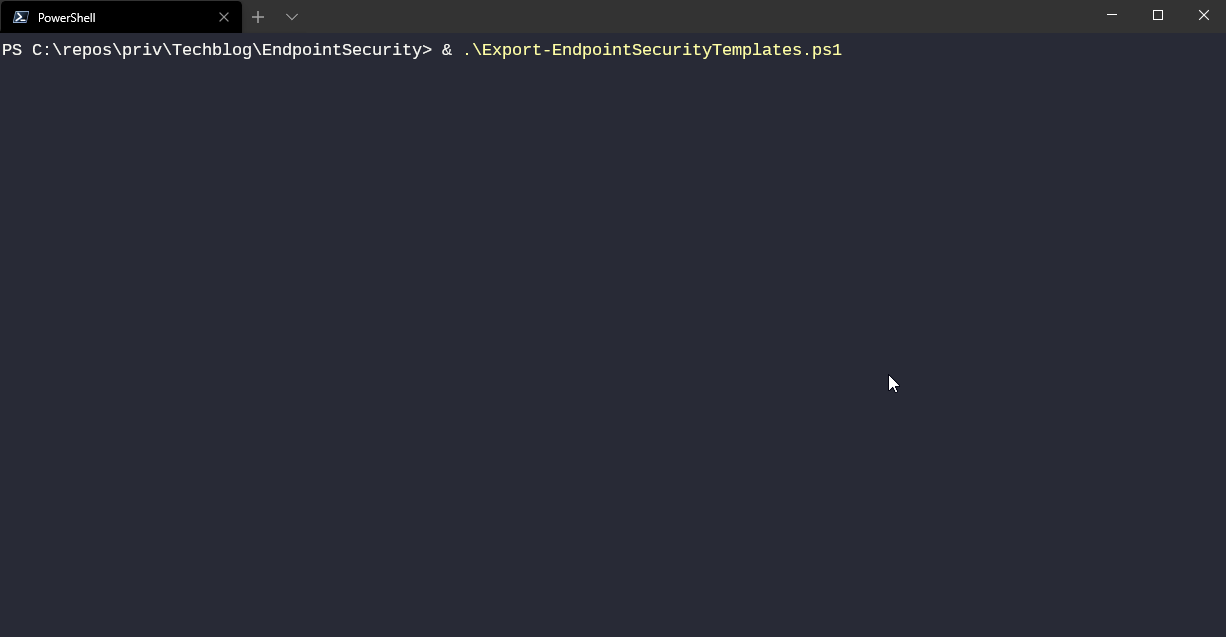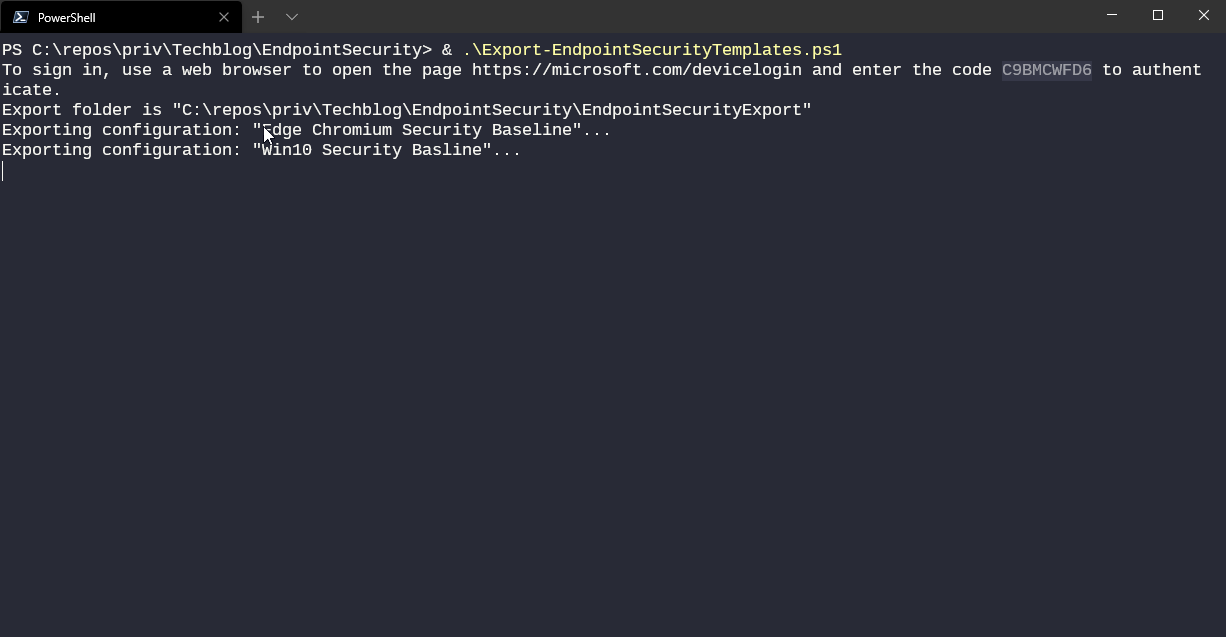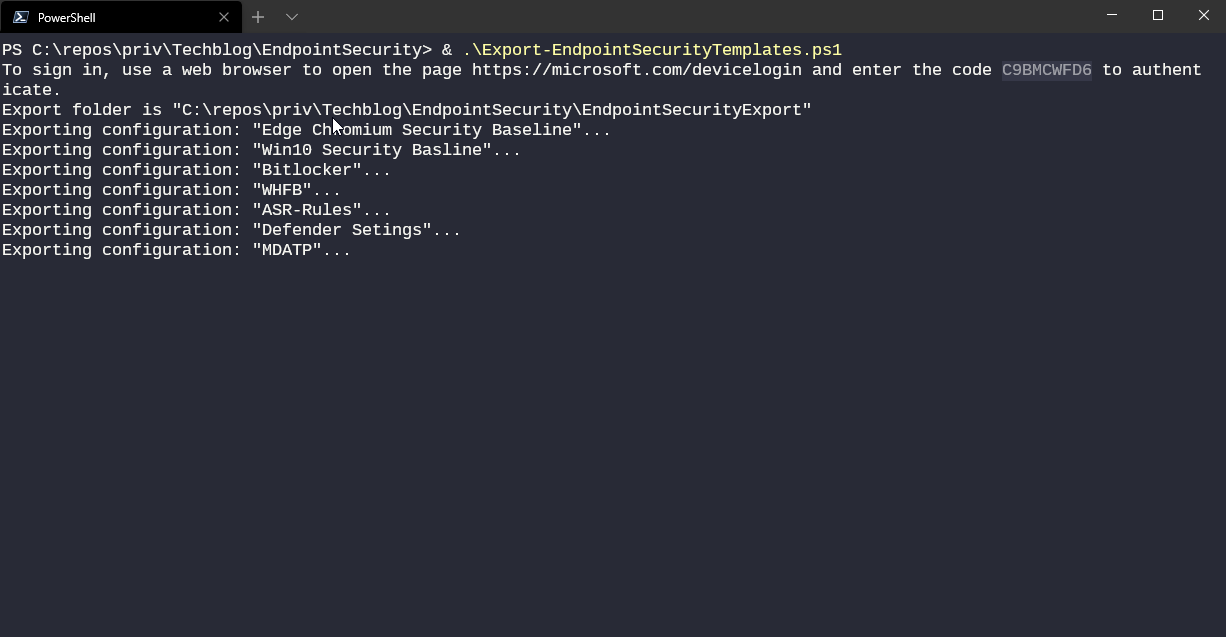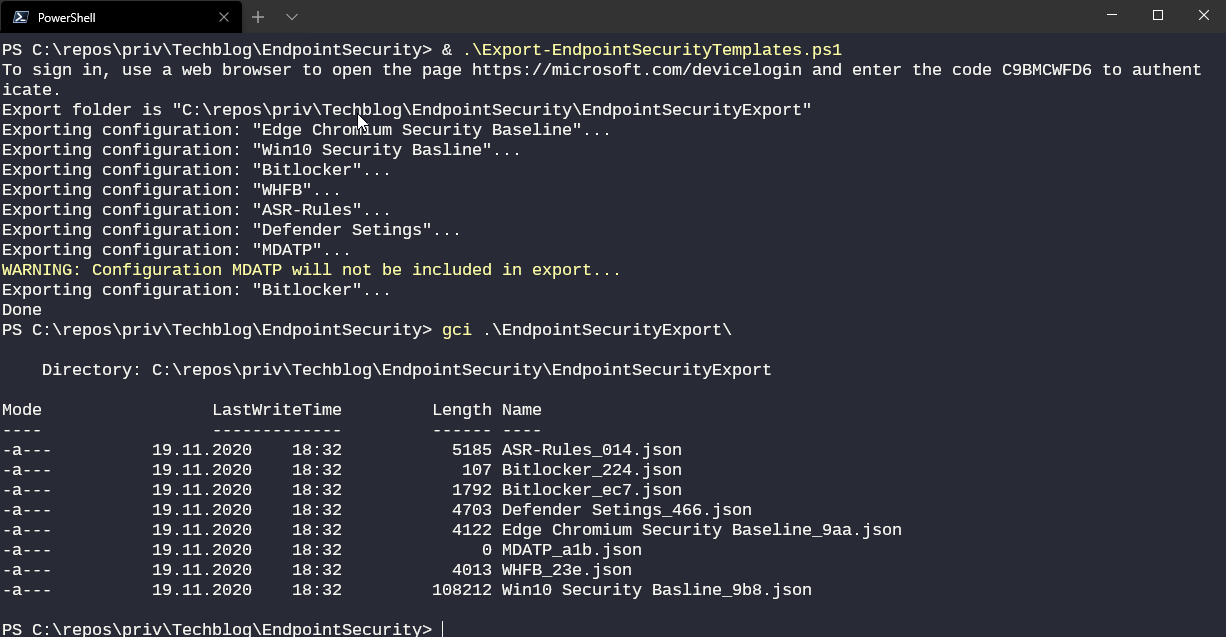
You can find the export and import scripts both on my techblog repository on GitHub. The scripts work for endpoint security profiles and security baselines. Endpoint detection and response configurations are not included (because of some tenant-specific oddities about onboarding info).
By default, exports are saved in a new directory that matches your script location.
The scripts are far away from perfect - if you want to tweak them I’m looking forward to PR’s on GitHub.
The scripts use the default Intune PowerShell app which should be enabled by default in your tenant. Depending on your PowerShell version and conditional access policies you might need to switch to another OAuth flow but this one can be easily changed.