As you might have noticed I have been doing quite a lot of automation stuff with Microsoft Graph for Intune and Azure AD. My preferred way to run PowerShell scripts which need to run on a regular basis is to use Azure automation. Unfortunately the official “Intune-PowerShell-SDK” does not support authentication with a client certificate. Therefore I updated the module and will show you how to use it with Azure automation.
Why I don’t like client secrets
Azure automation brings us service principals (run as accounts) which simplify the access to Azure resources by providing an Azure AD app registration and certificates to authenticate against Azure AD. This provides more security and prevents the risk from having client secrets stored as plain text in scripts. Going with a client secret when having a nice certificate based authentication solution in place feels like making a step-backwards for me. This was the main reason why I decided to “upgrade” the Intune-PowerShell-SDK to support certificate based authentication.
Why I love the Intune-PowerShell-SDK
This PowerShell SDK provides nice Cmdlets to do any kind of automation with Microsoft Graph, not only limited to Intune because it offers a helper cmdlets like:
Invoke-MSGraphRequest(perform any kind of Graph requests)Get-MSGraphAllPages(get all entries for requests which use paging)Connect-MSGraph(get an access token)
These helper cmdlets allow us to build scripts in a more standardized way. But as already mentioned the current release does not support client certificates. Additionally the cmdlets for this SDK are auto-generated from a .NET project.
Updated PowerShell module (SDK)
I forked the official SDK and added the possibility to acquire an access token with a client certificate. To do so I updated the “Connect-MSGraph” Cmdlet to accept “CertificateThumbprint” as parameter. The certificate must be available in the current users personal store.
The module is available on GitHub.
I also opened a pull request on the official repository and hope this will be integrated in the next PowerShell Gallery release of the SDK.
Set up Application based authentication for Intune
App registration
The manual process for creating an app registration is already documented by Michael Niehaus. The only thing that changes is that you do not need to generate a client secret.
When you create a new automation account in Azure automation it automatically creates a service principal (= Application Registration) in Azure AD.
You can also create a service principal afterwards on the automation account:
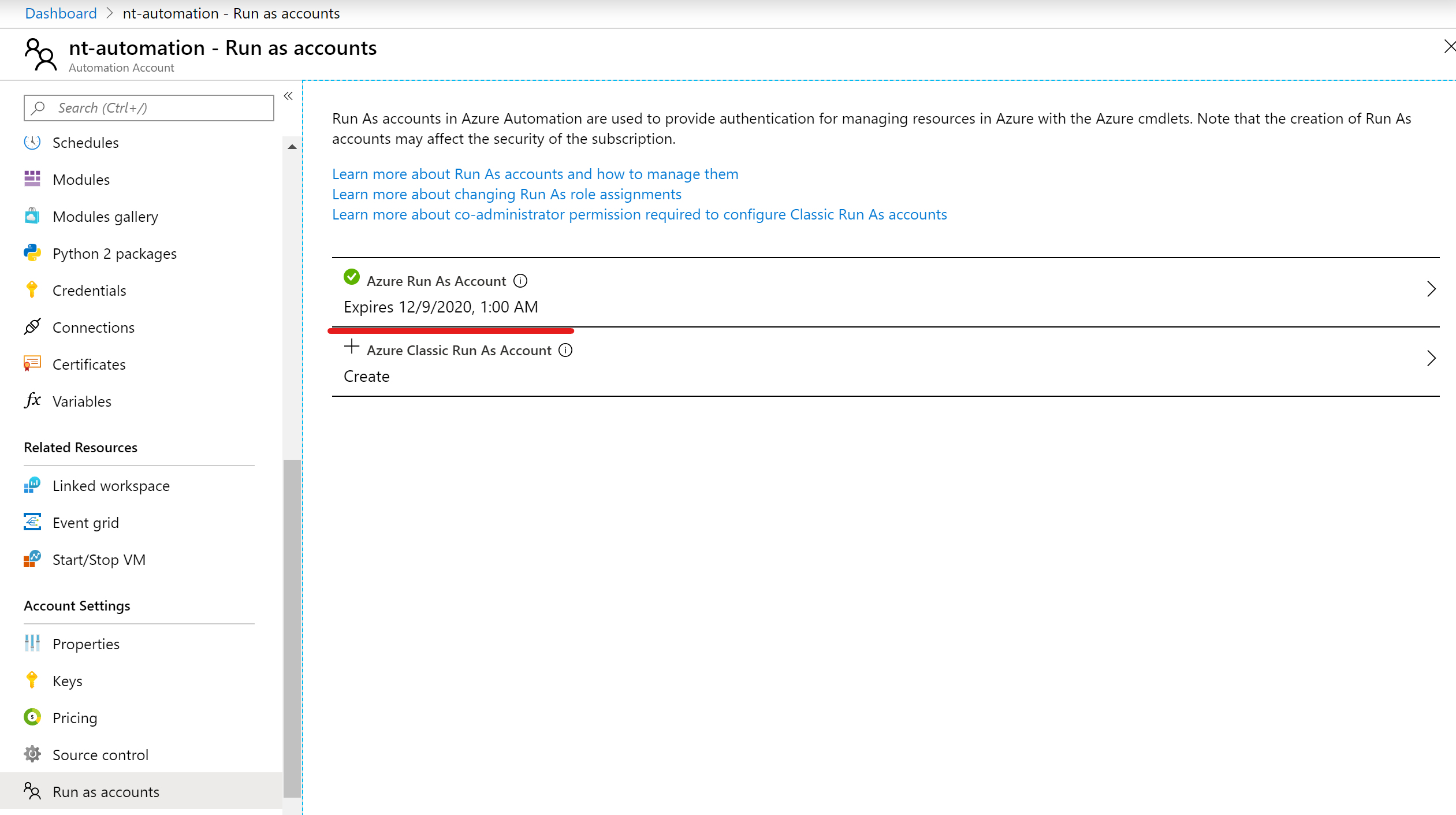
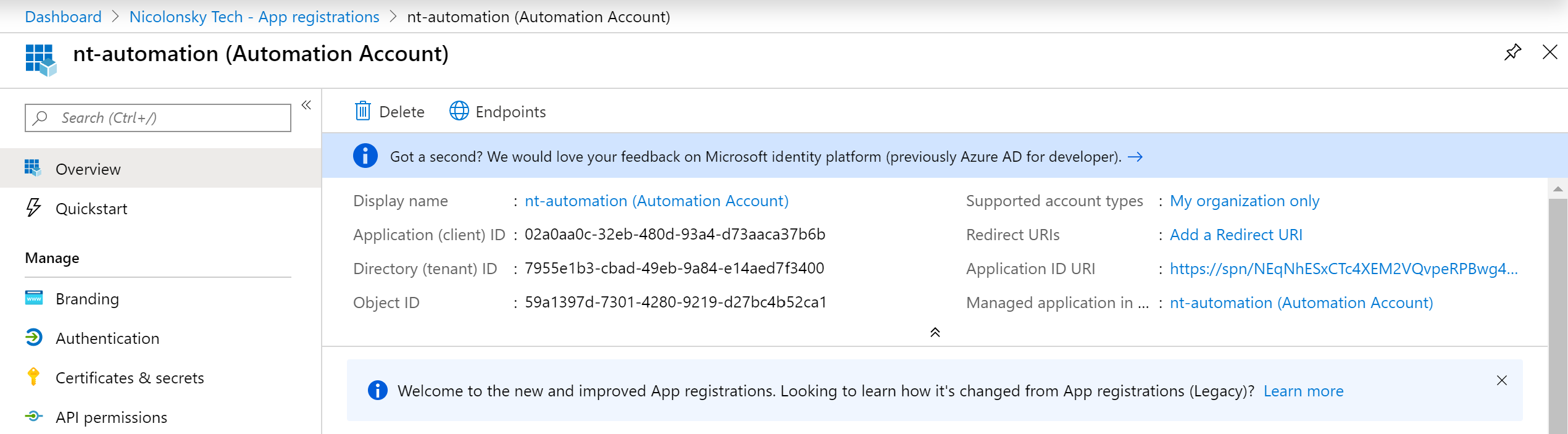
In Azure AD you will find then an application registration which starts with the name of your Azure automation account followed by a random sequence of characters (for better readability I always change the display name):
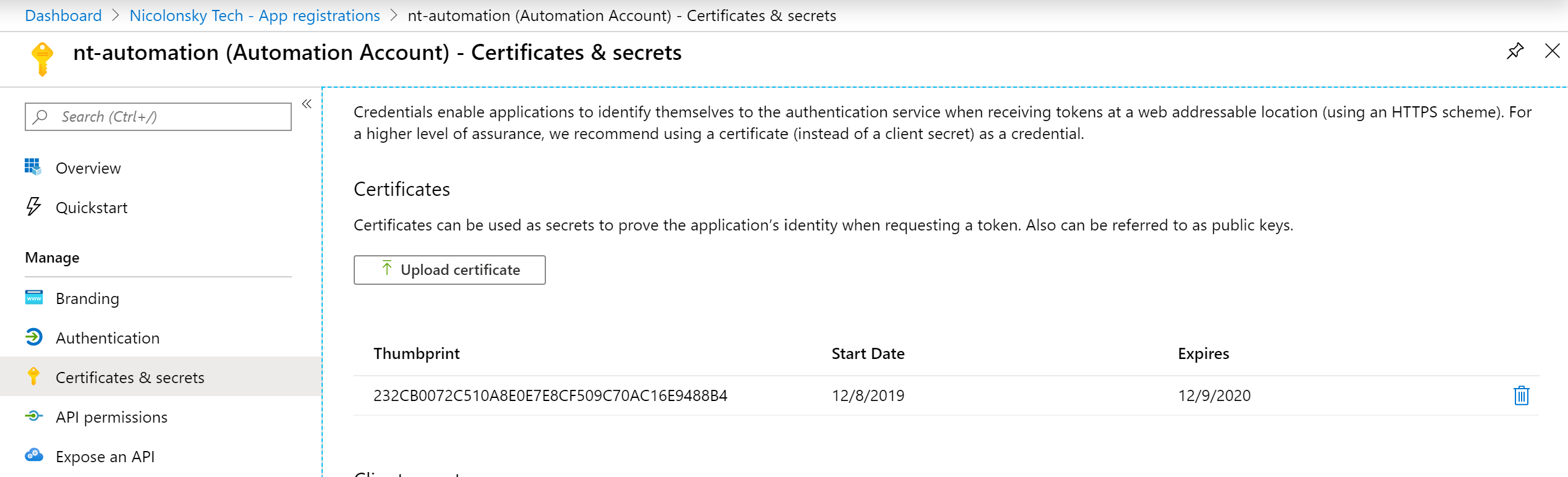
A client certificate gets automatically provisioned for the automation account:
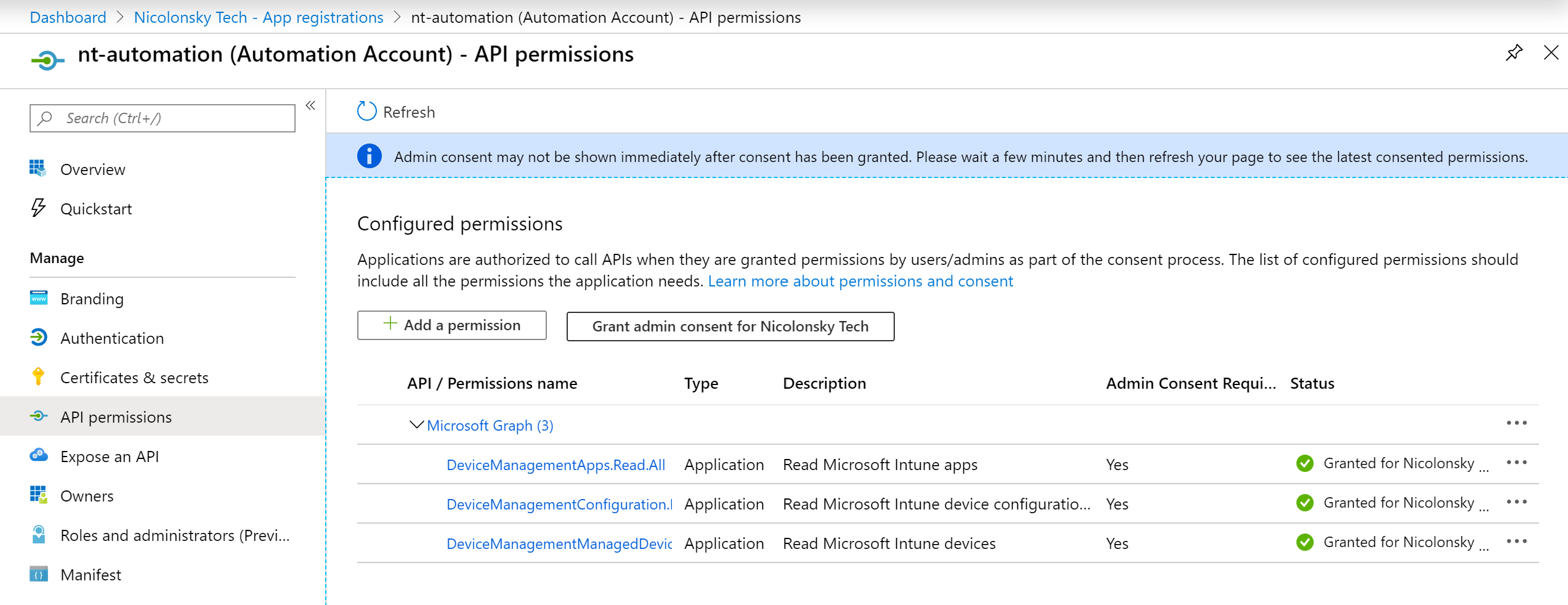
Last but not least assign the API permissions as needed to your App registration. Make sure to choose “Application” as designated permission type and do not forget to consent the added permissions afterwards! :
Upload the module from my GitHub fork and replace the “old” one if you were already using the Intune-PowerShell-SDK in your automation account.
Connecting from azure automation is quite simple. We just need to change the Microsoft Graph endpoint to our own tenant ID and use the automation account app registration. With the snippet below this all happens dynamically - no need to hardcode values:
Connect from Windows
If you have the “Intune-PowerShell-SDK” already installed overwrite the module files in "%ProgramFiles%\WindowsPowerShell\Modules\Microsoft.Graph.Intune\6.1907.1.0" with my fork from GitHub available here.
To connect from a Windows machine we need to generate a new certificate and install it to the users personal store, export the public key:
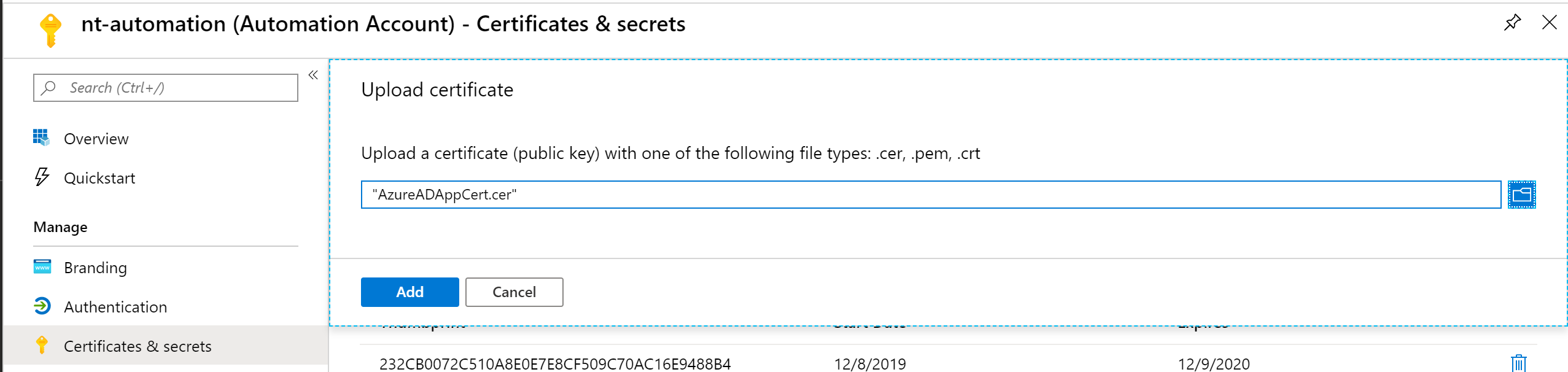
The exported public key needs then to be uploaded to the app registration:
Now you are almost ready to connect to the Microsoft Graph API. But you need to specify your tenant and application ID before you can connect (both ID’s can be viewed on the overview of your app registration):
Update-MSGraphEnvironment -AppId "02a0aa0c-32eb-480d-93a4-d73aaca37b6b" -AuthUrl https://login.windows.net/7955e1b3-cbad-49eb-9a84-e14aed7f3400
Afterwards you are ready to connect with your client certificate:
Connect-MSGraph -CertificateThumbprint ACF2224FD67163218DA9BE82E66D71733A91E80C
Happy Microsoft Intune PowerShell SDK-Ing with certificates!