Recently I read a great article from the Microsoft IAM Director Sue Bohn concerning a Conditional Access Q&A. One question was about the device platform feature - which let’s you apply a policy only to a specific device platform like iOS, Android or Windows 10.
The detection of the device platform relies on the user agent string sent by the application or web browser. Because this one can be spoofed easily better configure your Conditional Access policies wisely.
The problem
As soon as you enable the device platform selection there’s the chance that a user doesn’t catch any Conditional Access policy.
As a result, you should not rely on the User Agent String to be present or to be accurate. Most browsers have a function to set an arbitrary User Agent String for testing purposes. (Microsoft)
Bypass example
To give you an example, here’s a little walk-through:
- Conditional Access Policy configured for all cloud apps
- Windows 10 selected as device platform
- Access control: Block
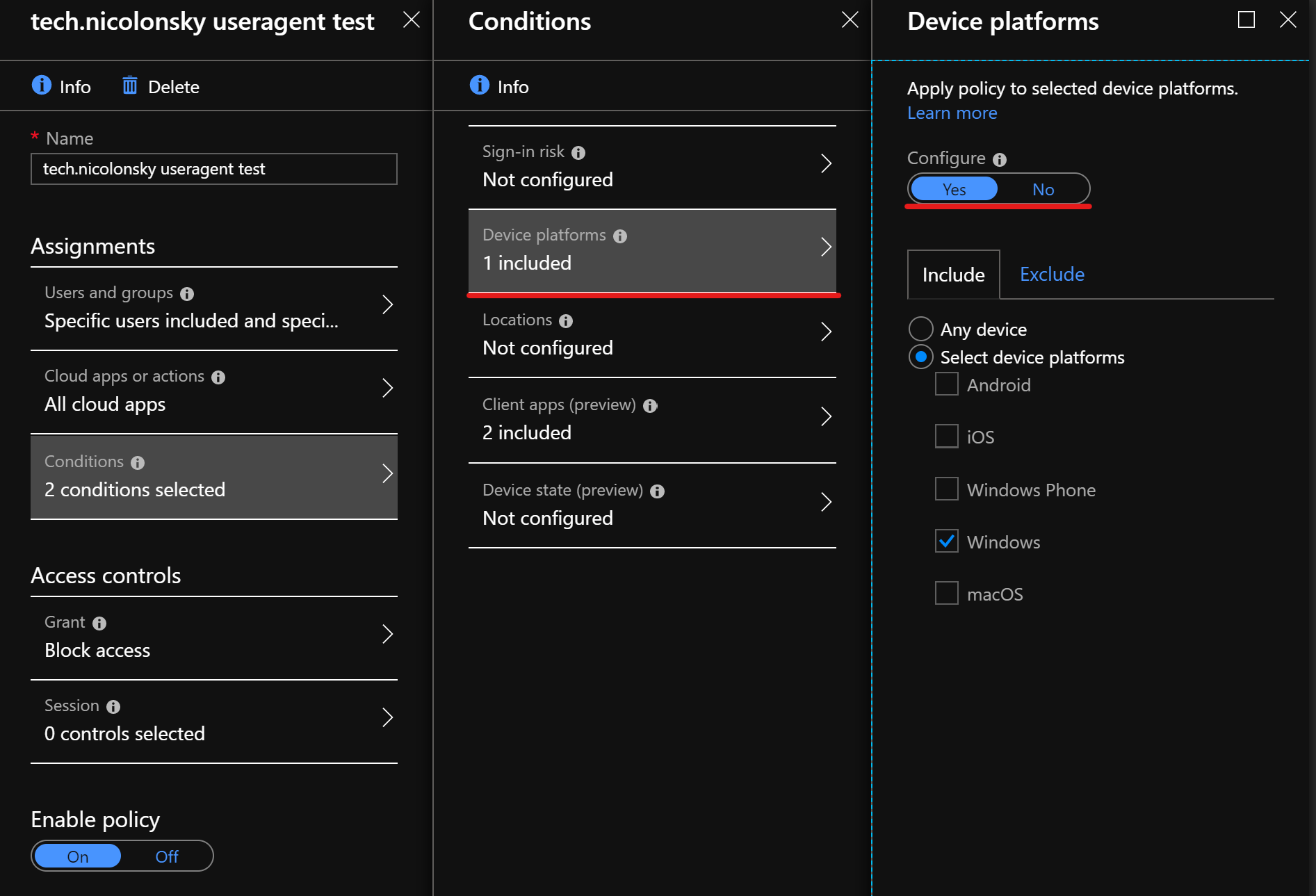
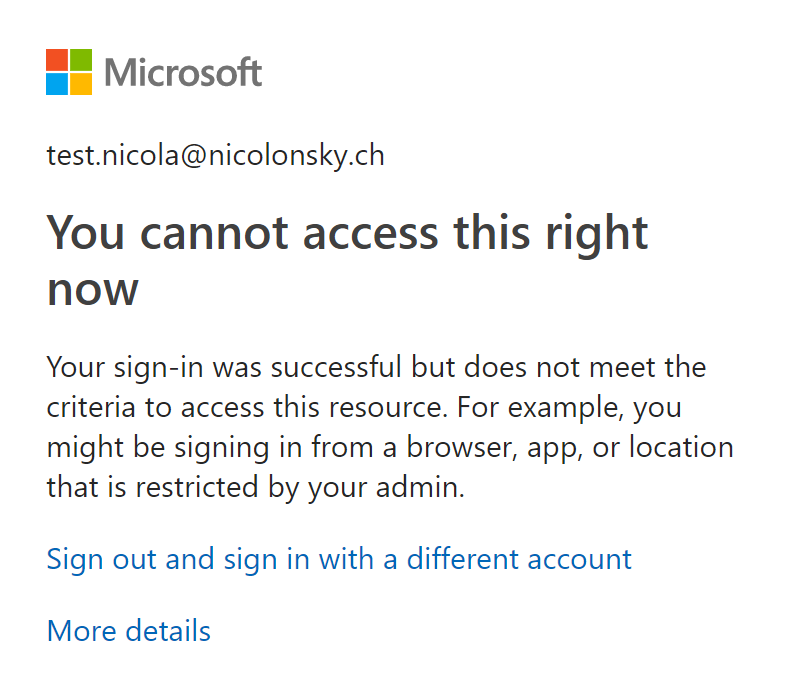
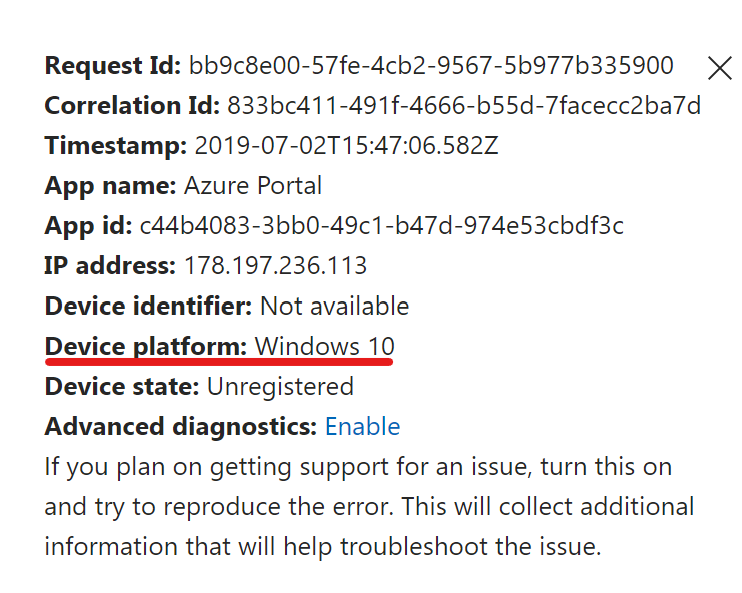
If we now try to access the azure portal with a Windows 10 app or browser we get the following result:
|  |
|  |
|
Now let’s change the user agent string with the developer settings and the browser of your choice to an iPhone:
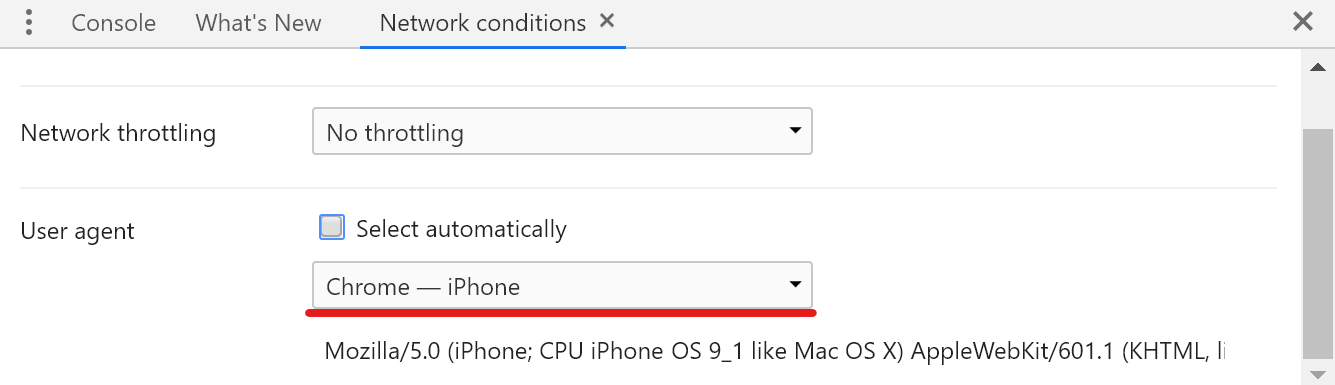
and try to access the azure portal again with our new user agent:
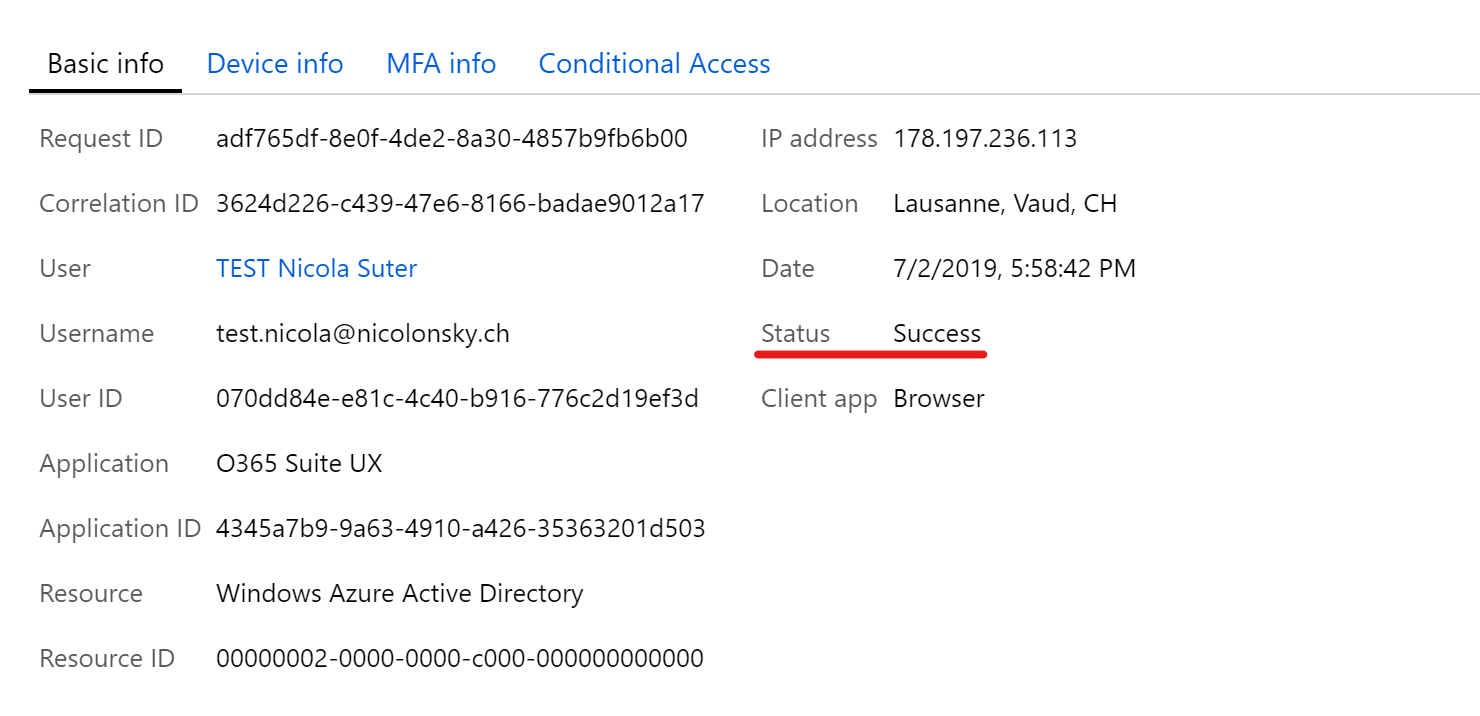
We have a successful sign in which can be tracked in the Azure AD sign-in logs.
How to avoid Conditional Access platform bypass
- If you intend to use the Platform selection feature make sure that there’s an conditional access policy applicable for every platform
- Be aware that if a device or application doesn’t fall into the common platforms (Android, iOS, Windows Phone, Windows, macOS) no policy applies without further configuration
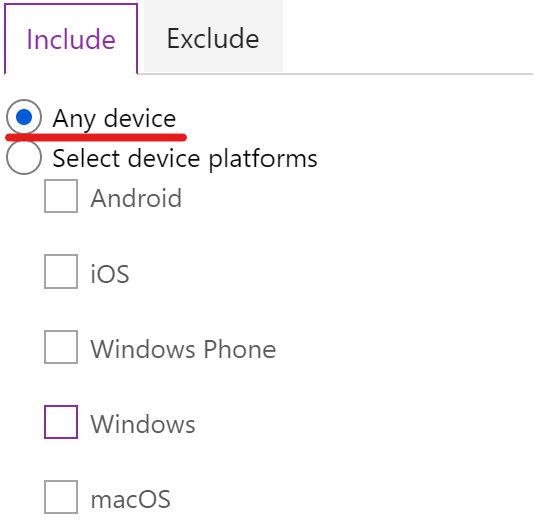
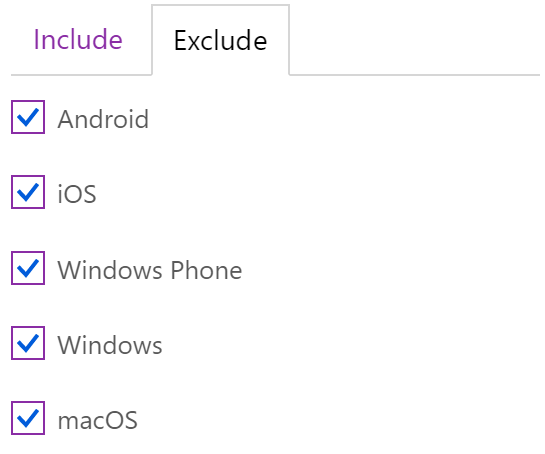
- Build a Conditional Access policy which blocks access for unknown platforms by including the “Any device” category and excluding the platforms you want to configure separately
| |
|  |
|