An account in your Azure Active Directory got deleted and you want to examine who initiated the delete action? Sounds very simple but if you do not want to search your logs manually things become a little bit trickier.
The challenge
When a user gets deleted and you only remember it’s userPrincipalName you wont be able to to search for a match. And I doubt that you memorized the Azure AD object id of that user.
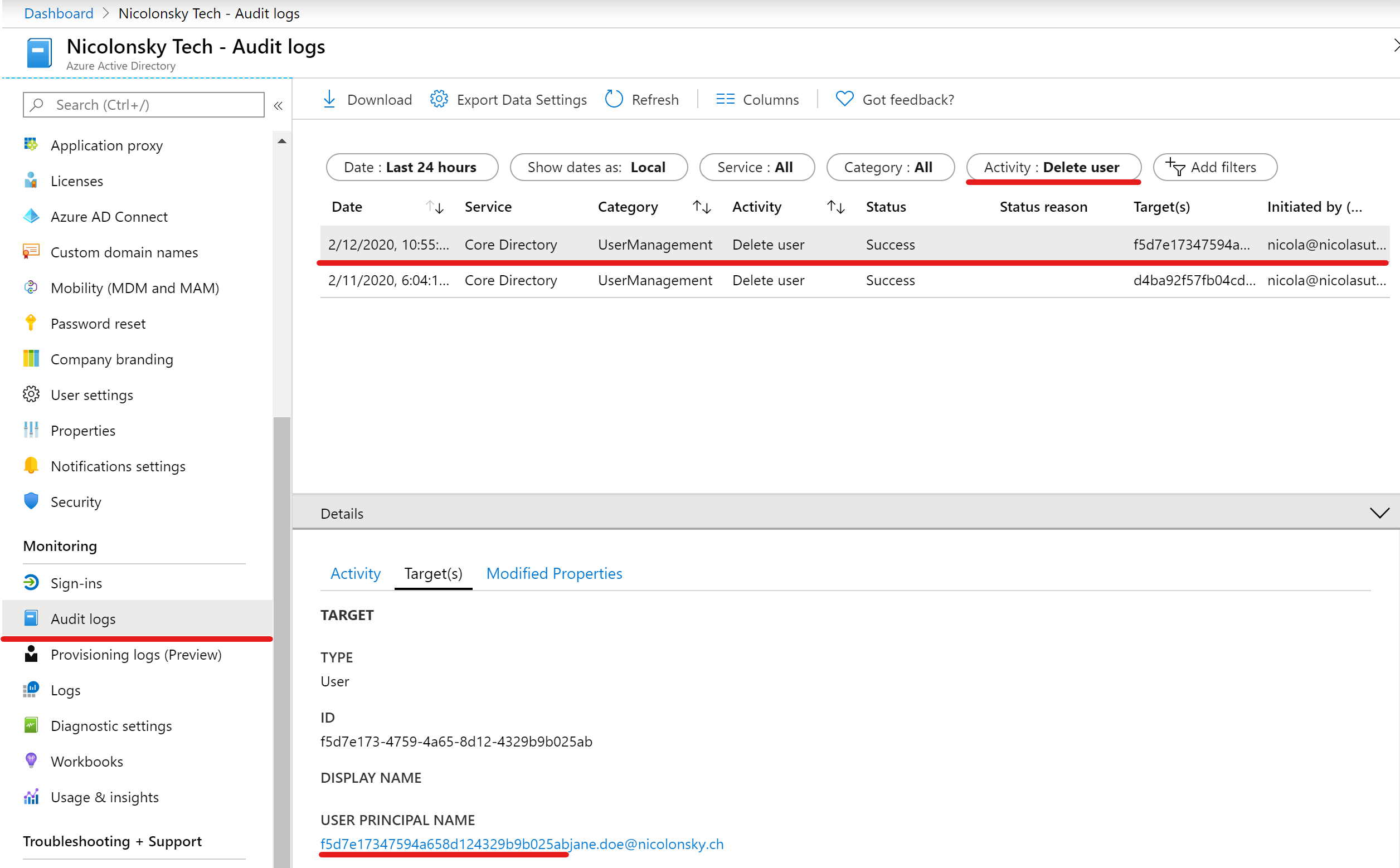
Here’s what the Azure AD Audit log shows us:
The userPrincipalName attribute will get the Azure AD object ID as prefix:
- userPrincipalName before deletion: [email protected]
- userPrincipalName after deletion: [email protected]
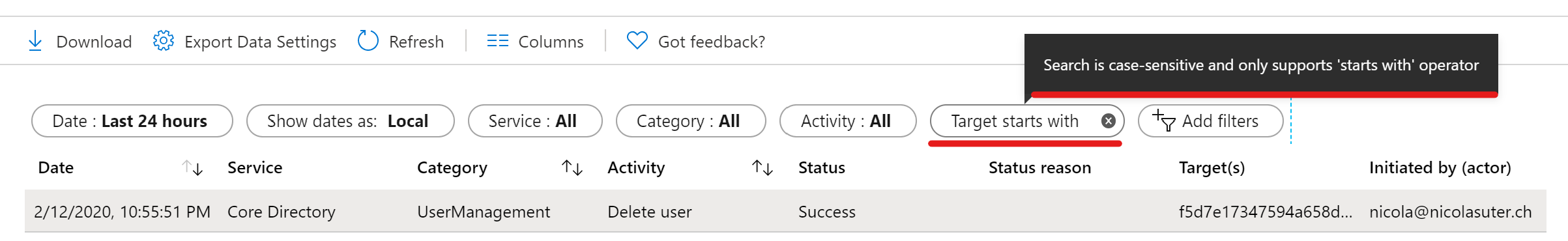
By having a closer look to the Azure Active Directory Audit logs you will notice that the filtering or search capabilities are limited in terms of searching for a specific target:
Search is case-sensitive and only supports ‘starts with’ operator
Which means we cannot search for the userPrincipalName. The only option in the Azure AD Audit Logs would be to download the logs and perform a search within a text editor which is not really feasible nor efficient.
Note: Azure AD Premium (P1 / P2 plans) retains audit and sign-in logs only 30 days! Source.
If you are not forwarding your Azure AD audit logs and you do not have an SIEM or monitoring solution in place it is the call to action to deploy an Azure Log Analytics Workspace!
Azure Monitor (Log Analytics)
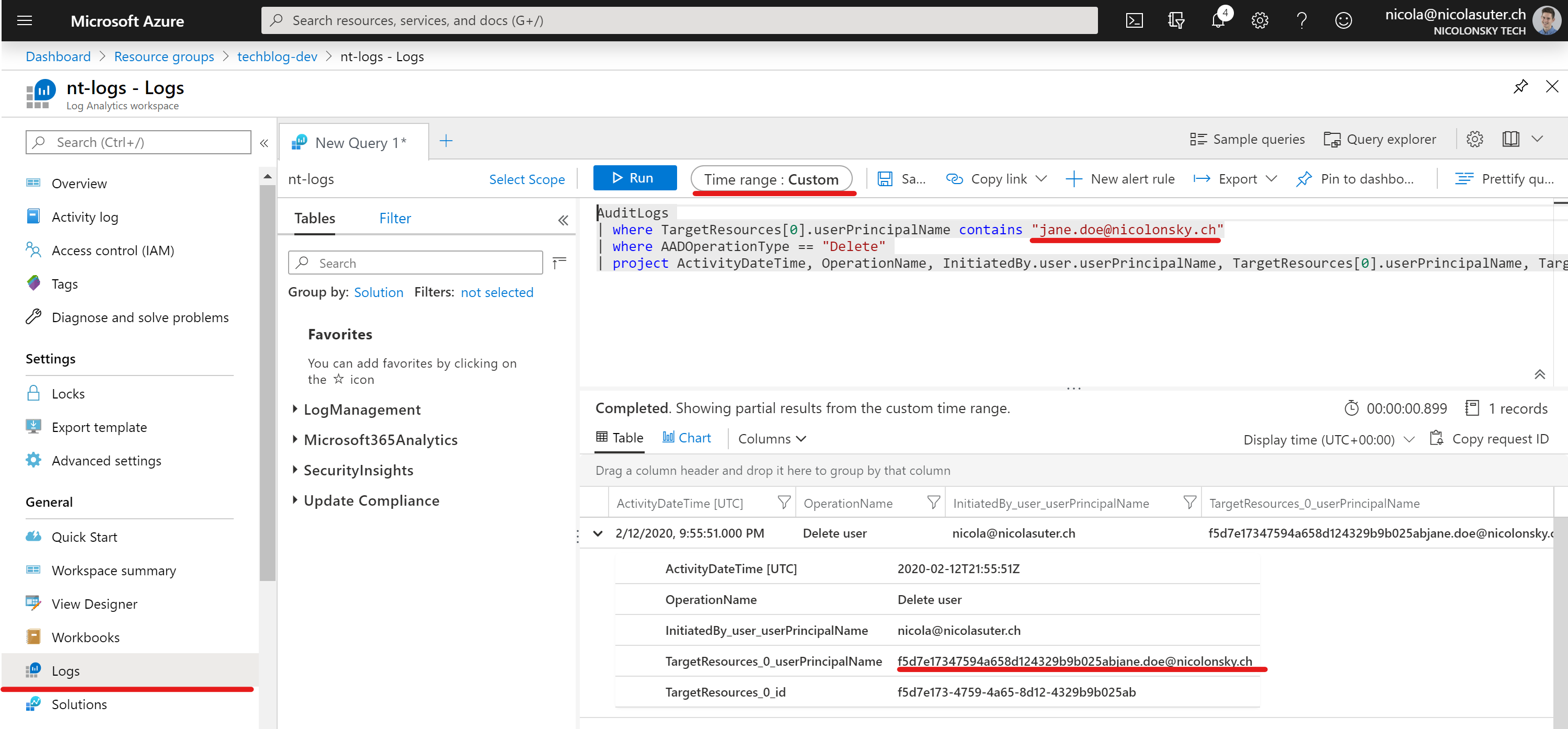
Searching for a deleted user in Log Analytics with KQL (Kusto Query Language) is definitely more feasible and allows us to search for the userPrincipalName with the “contains” operator.
| |
Takeaways
- Retain your Azure AD audit logs for a sufficient time (easiest and cheapest way is probably Azure Monitor / Log Analytics)
- If you are using Azure AD Connect and investigating deleted hybrid identities the Azure AD Audit logs will not help you because the Azure AD Connect account replicates directory changes –> Investigate your on premises Active Directory logs
- Did I already mention that you should deploy a Log Analytics Workspace?