The Azure AD portal does not really provide an overview about all directory role assignments in your tenant. If you want to review existing Azure AD Directory roles a csv report will probably better server your needs. Therefore I created a PowerShell script to export the role assignments.
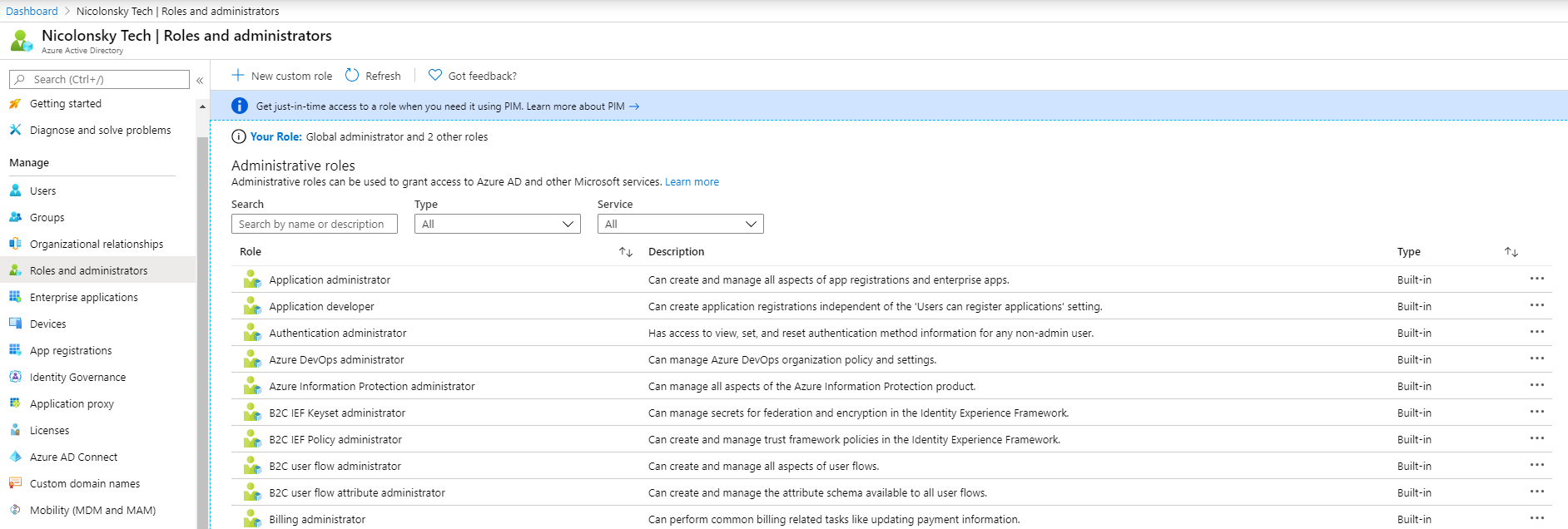
Find the PowerShell script in my techblog GitHub Repository.
Make sure that you have the AzureAD PowerShell module installed before running the script. You can install it by running “Install-Module AzureAD”.
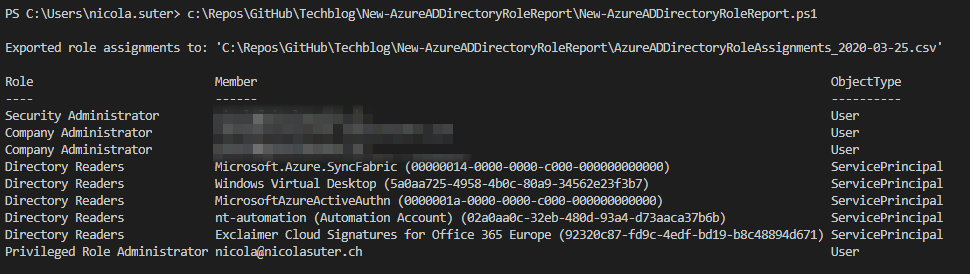
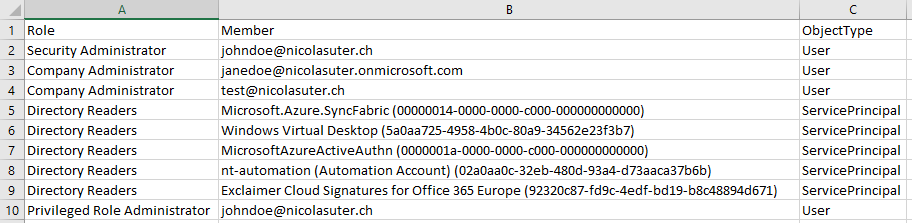
Report
The report contains three columns:
- Role (name of the directory role)
- Note that the Global Administrator Role is represented as Company Administrator
- Member
- If the role is assigned to a user its the UserPrincipalName
- If the role is assigned to a service principal its the display name with the Azure AD application ID in the brackets
- ObjectType
- Indicates whether the role is assigned to user account or a service principal
Comparing reports
You can compare two reports with the following PowerShell code:
| |
Counting assignments per directory role
If you want to count how many times each role is assigned, e.g. how many times is the Company Administrator (Global Administrator) role assigned you can process the date stored in “$roleAssignments”
| |
Other approaches
An even better approach is to use Azure AD Access reviewswhere users need to confirm their assigned directory role on a regular basis to keep it:
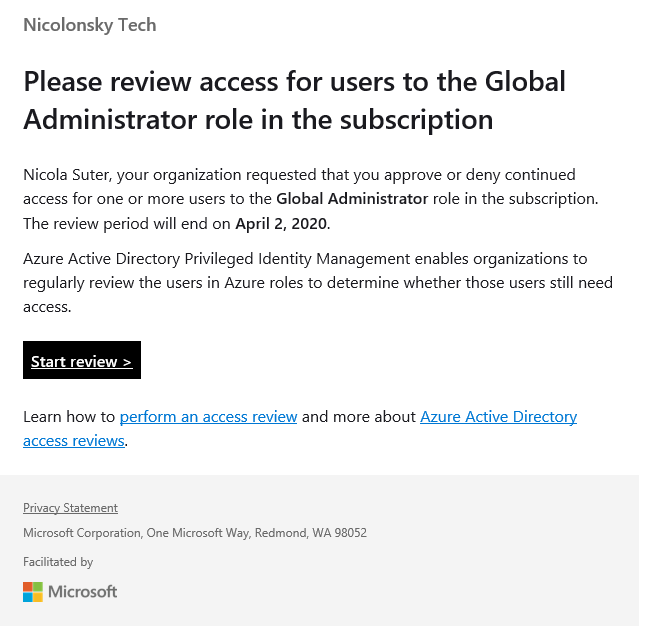
The downside here is that it requires Azure AD Premium P2 licenses .
Final words
Generating a report of assigned directory roles can provide you good insights and also be a motivation to verify if you’re really following the least privilege approach.
To end this post I have three questions as a take away for you which hopefully support your review process of the report:
- Are new built-in roles available which better suit required permissions? Are you really using least privilege? (See Administrator role permissions in Azure Active Directory)
- Have you considered Azure AD privileged Identity Management (PIM)?
- Could you use service specific RBAC features with fine grained permissions instead of directory roles?