When you are new to RESTful APIs and want to start with Microsoft Graph to automate tasks in your Endpoint Manager tenant all the stuff about app registrations, access tokens, pagination and request headers can be quite confusing. In this post I want to show you a quick tip to kickstart your Microsoft Graph API experience.
Requirements
- Cloud admin account with Intune Administrator role assigned
- Ability to install Modules from the PowerShell gallery
JWT
Just because you can’t see it… doesn’t mean it isn’t there: Due to the naturality of OAuth 2.0 and OpenID connect (these are the protocols involved for authorization and authentication in a cloud environment) we can capture short lived access tokens, also called Json Web Tokens (JWTs) directly from a browser. Tokens are usually valid between 50 and 60 minutes - just what we need to get some hands on with Microsoft Graph API and MEM automation.
The cool thing is actually that we don’t need any kind of app registration or additional permissions which can be quite some blocker in certain restricted environments (or staff unfamiliar with those technologies 😉).
Modules
We can easily install the required Microsoft Graph Modules for the MEM area with the following command:
| |
Let’s connect
To obtain the JWT:
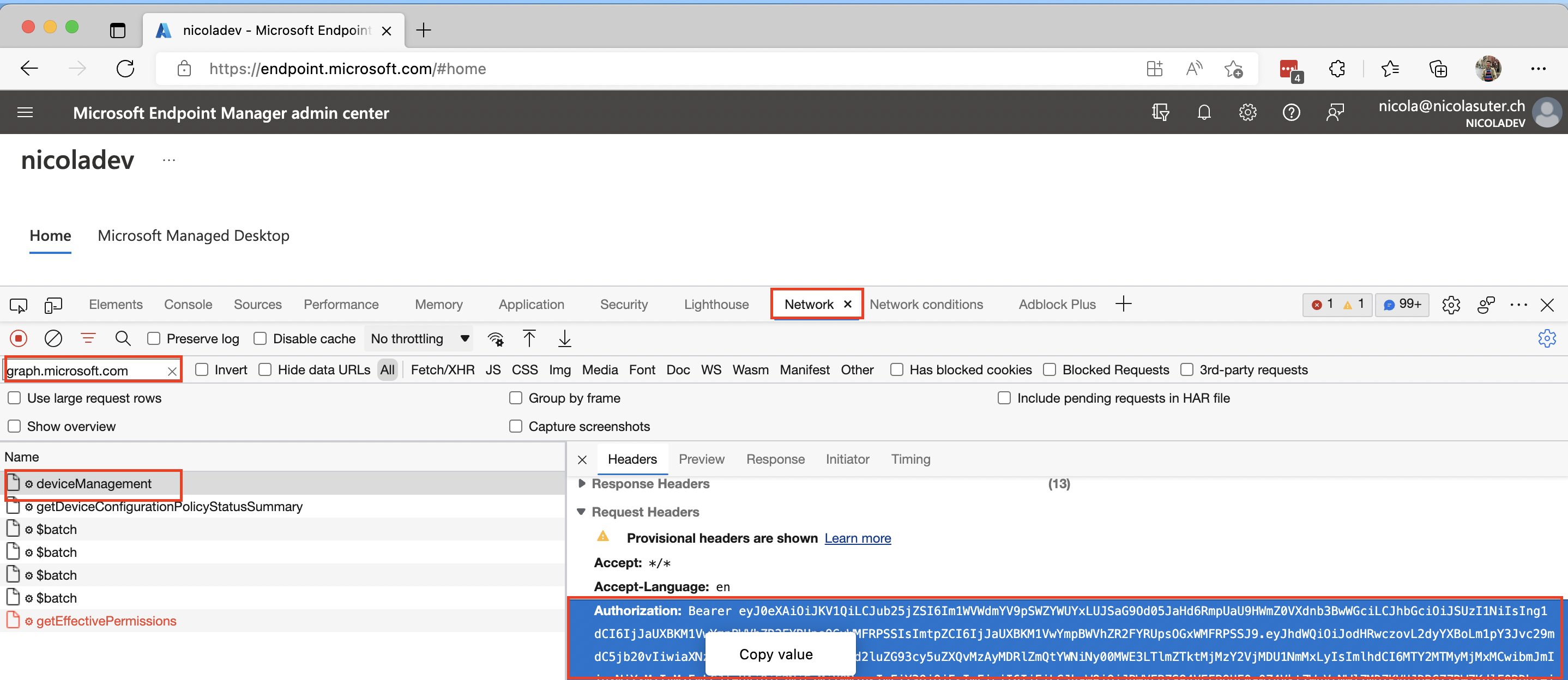
- Visit Microsoft Endpoint Manager Admin Center
- Start your browsers dev tools (usually F12 key)
- Visit the network section
- Enter:
graph.microsoft.comas filter - Reload the page (via reload button or F5 key)
- Select the first request
- Copy the Authorization header value
- Enter:
To tell the Microsoft Graph PowerShell SDK about our access token we can simply connect with:
| |
… and we can start to query data from the API, for example getting a list of all managed devices:
| |
That’s probably the most simple way to get started with the Microsoft Graph PowerShell SDK! Additionally this is supported for lots of permissions you have assigned to you administrative account as the JWT contains the Directory.AccessAsUser.All scope. Furthermore, this approach works for all scenarios, even if an organization has not allowed apps like the Microsoft Graph Explorer or prevents you from creating custom app registrations.
In case you want to know more about how to connect interactively or by creating your own app registration you can find more details in a post I published a while ago.