While fine-tuning and adjusting applocker policies for co-managed Windows 10 clients I got really annoyed by special characters commonly used in the German/Swiss language. The Intune portal seemed to use different encoding and didn’t allow me to just copy/paste the currently deployed policy and extend it with a new rule. I needed to request the original file that was uploaded to the tenant in order to adjust the rule. Instead of just accepting this I decided that it is time for an easier approach which I will share with you.
The actual issue
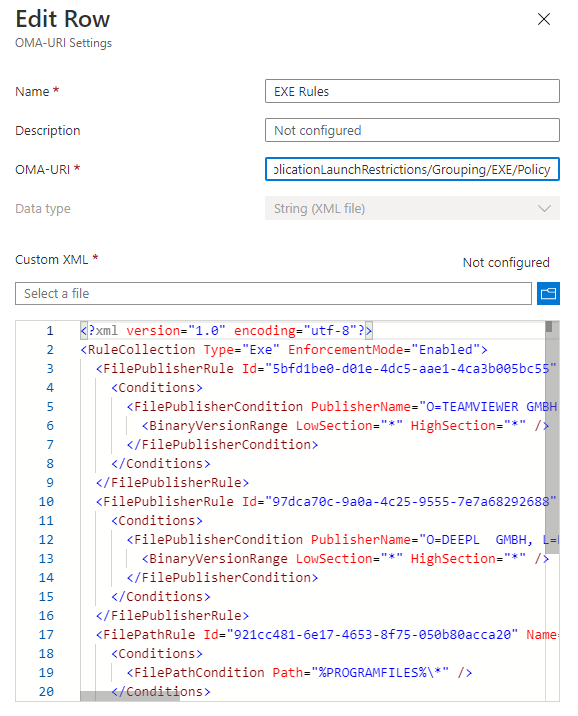
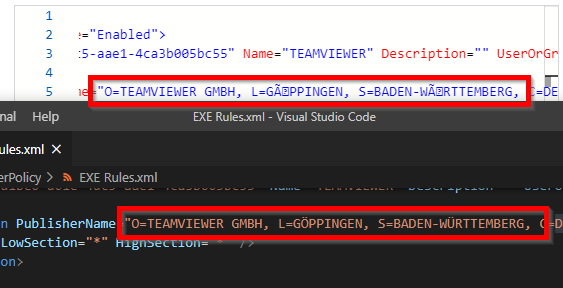
After uploading the XML with the applocker policies (in my case EXE rules), special characters like ‘ö’ or ‘ü’ have a weird encoding displayed in the portal. The next person that wants to edit the policy needs to take care to fix the unrecognized characters otherwise the publisher rule won’t work anymore.
Top: Portal view of the special characters, bottom: original file.
Fixing things
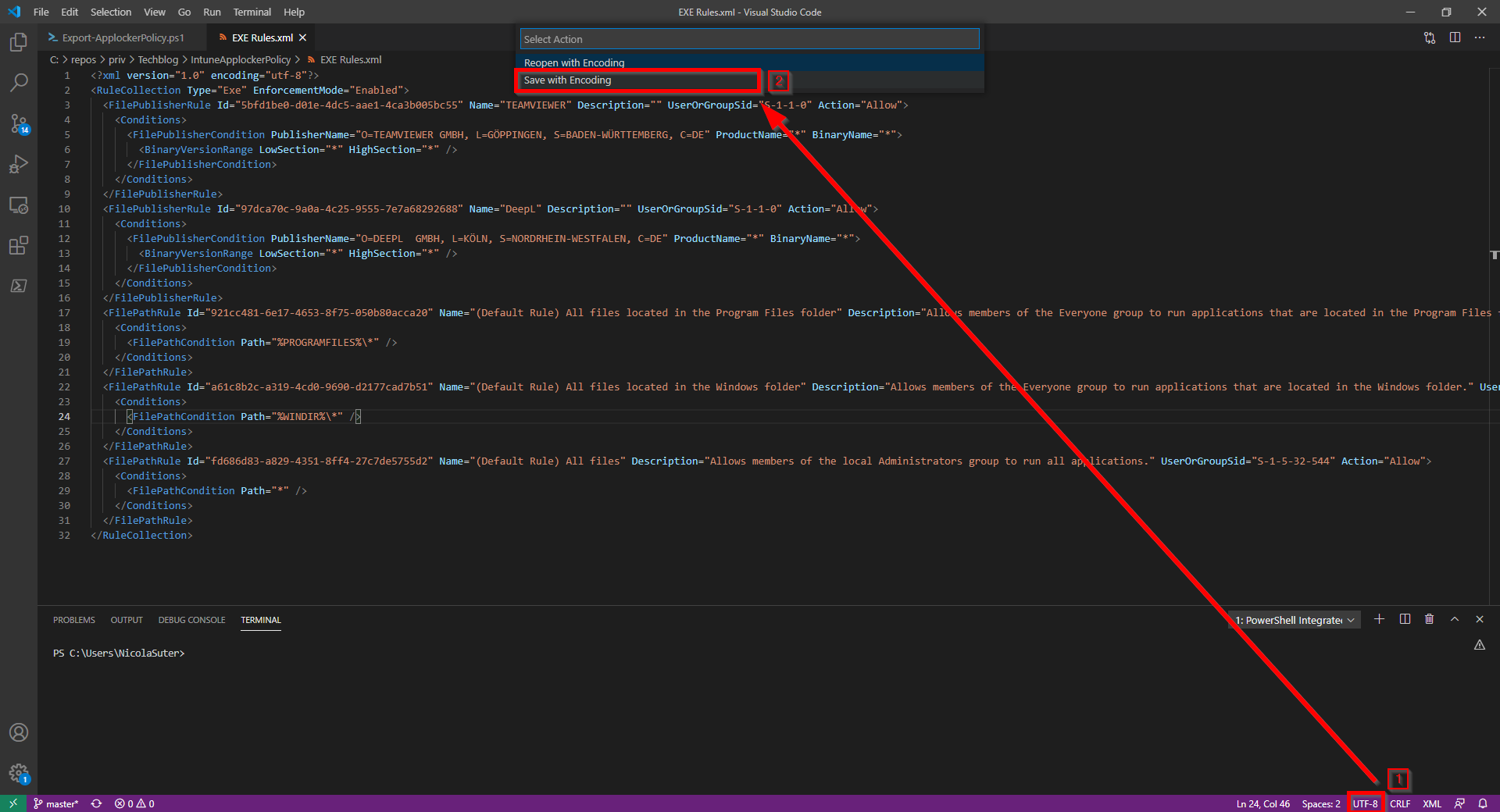
Save file with UTF-8 encoding
First, make sure that you saved an uploaded the file with UTF-8 encoding as this introduces support for most character sets. You can do this by selecting the encoding box in the right bottom of Visual Studio Code:
How to retrieve the XML value
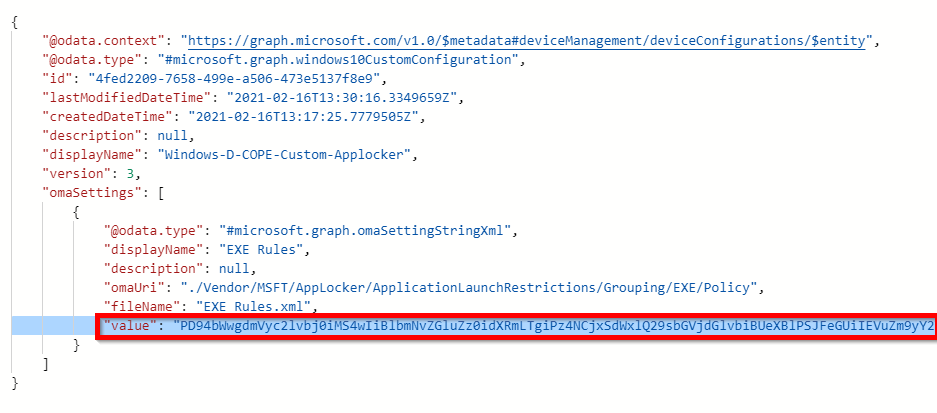
After visiting the Microsoft Graph explorer and the configuration profile: GET: https://graph.microsoft.com/v1.0/deviceManagement/deviceConfigurations/4fed2209-7658-499e-a506-473e5137f8e9 I understood that the uploaded XML content is served as base64 encoded string from the Graph API:
A pinch of PowerShell
Of course, we could decode the base64 string we just discovered on the API with an online tool but this would mean that we need to visit Graph Explorer and the base64 decoding tool each time when we want to adjust the policy. With PowerShell we have all the tools we need to make the API requests and decode the base64 to an XML file.
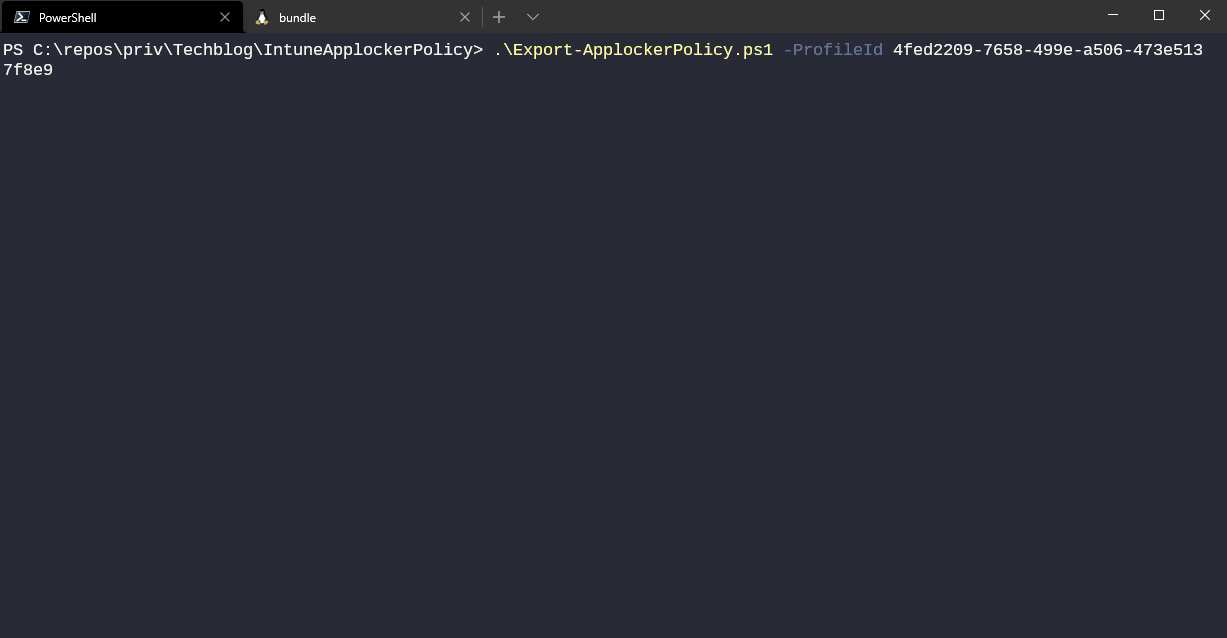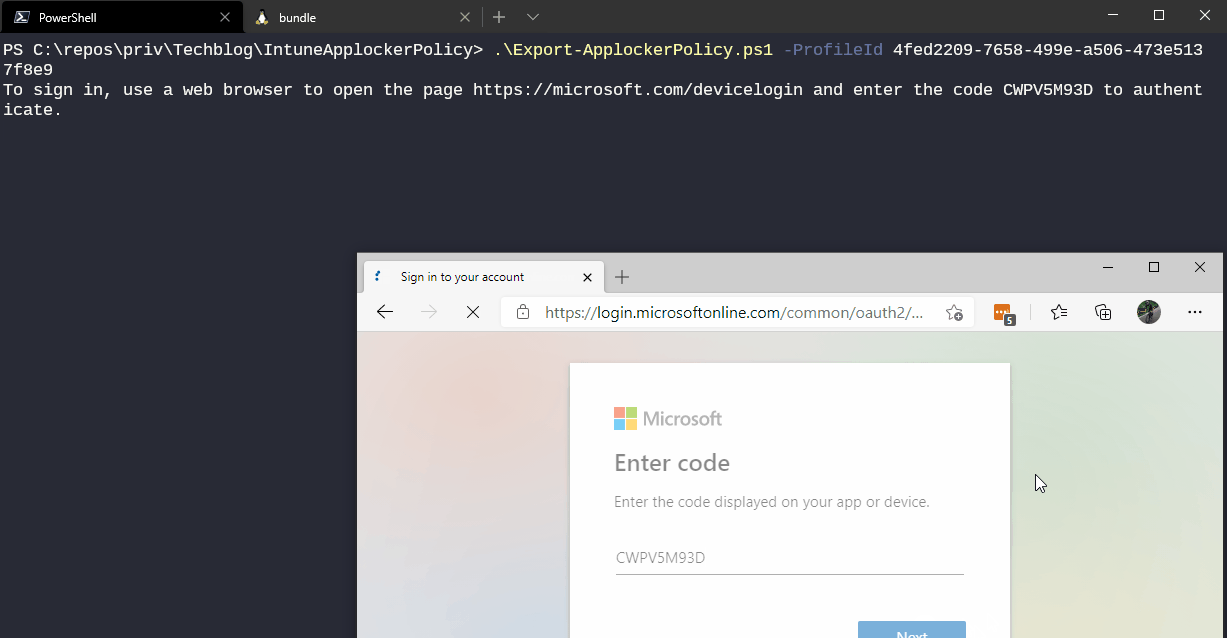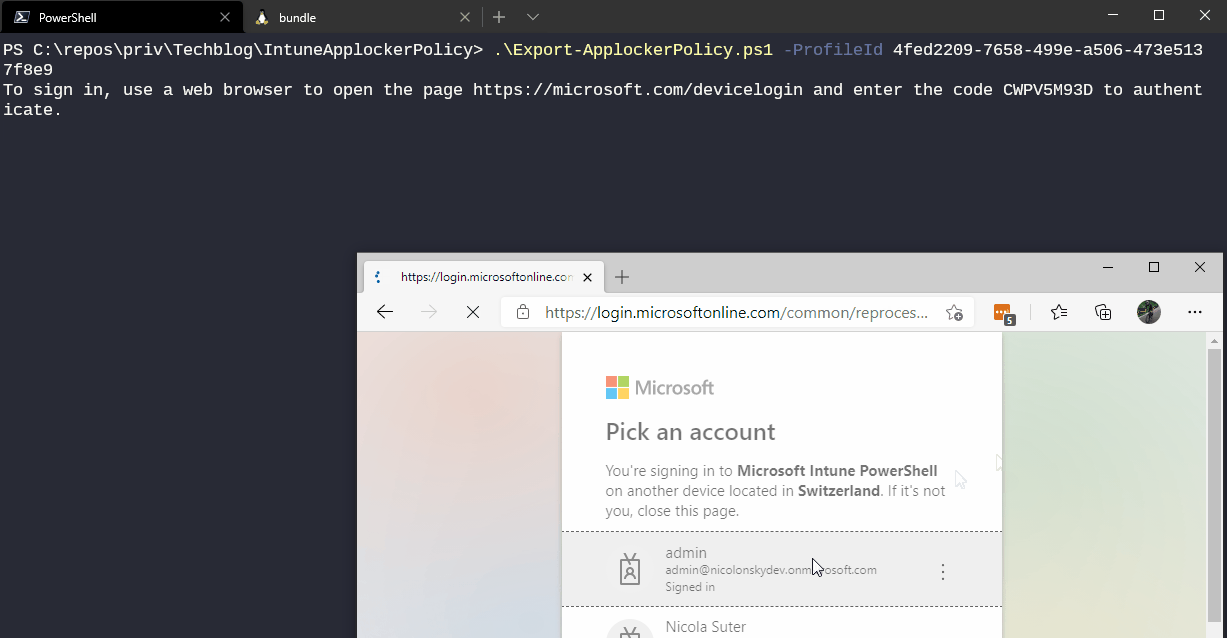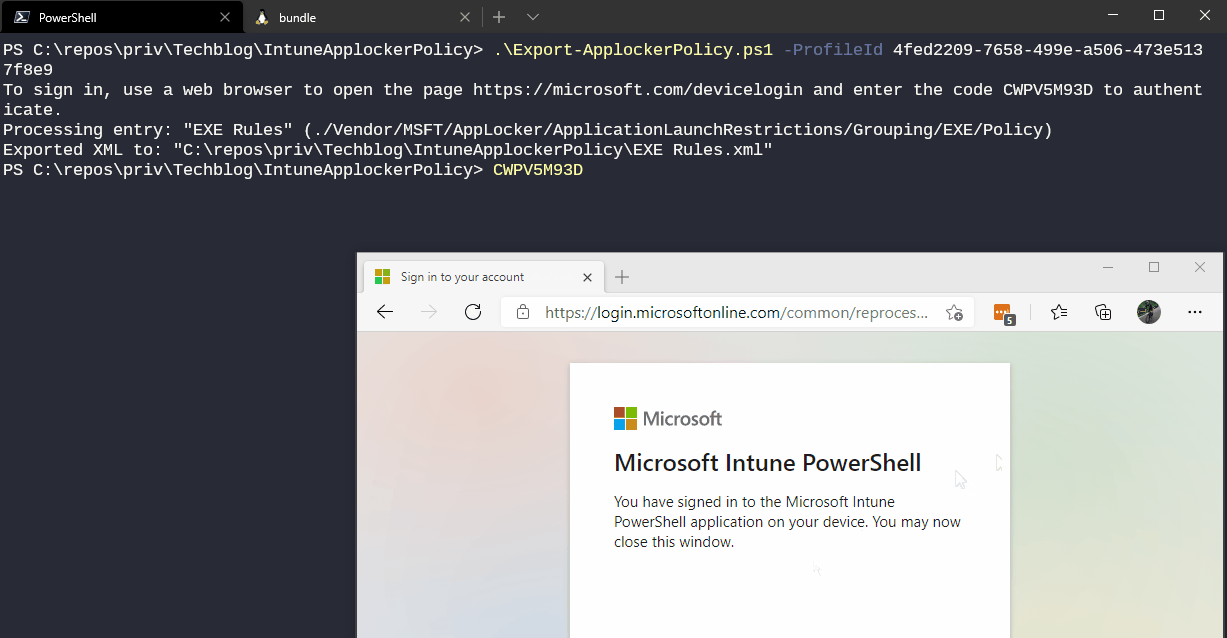
So check out the Export-ApplockerPolicy script on my techblog repository which does all the magic and pulls the content of your OMA-URI and saves it decoded to the script location. You only need to pass one script parameter called -ProfileId <GUID> which holds the ID of the configuration profile.
You can easily copy the ID when you have opened the configuration profile in the web browser: https://endpoint.microsoft.com/#blade/Microsoft_Intune_DeviceSettings/ConfigurationMenuBlade/properties/configurationId/4fed2209-7658-499e-a506-473e5137f8e9/….
As a prerequisite for the script you need to have the MSAL.PS PowerShell module installed which handles the access token acquisition for the Graph API.
Conclusion / Recap
I hope this solution saves you some time to edit your applocker policies deployed with Intune. As a little recap, make sure that you initially upload the file with proper UTF-8 encoding and don’t worry that the content is still displayed with funny characters after using the solution described here. You can now easily export the applocker policies (with the right encoding and special characters), make your changes and re-upload the file to the Microsoft Endpoint Management portal.